Microsoft Outlook Forensic Analysis Tool
Outlook Forensic Toolbox
Outlook Forensic Toolbox helps restore e-mails, appointments, attachments, contacts, tasks, notes, calendars, journals and other from damaged PST or OST files from Microsoft Outlook
- Rating
- (10)
- (1)
- (0)
- (0)
- (0)
Outlook Forensic Toolbox is designed to reveal hidden and deleted information from Microsoft Outlook data files (files with PST and OST extensions). The tool performs forensic analysis of Microsoft Outlook data stores, in which all objects are saved: letters, contacts, reminders, files, attachments, and more.
Outlook Forensic Toolbox retrieves deleted and hidden data that is not exposed under normal viewing of PST / OST files in Microsoft Outlook.
An array of hidden information:
- whole letters
- contacts
- attached files
- meetings
- reminders
- tasks
- notes
- calendar
- magazines
Or partly restored objects or service information from objects as well:
- service headers of letters
- text fragments
- parts of files
- parts, fragments, or blocks of letters
- nested objects
The principle of the program is to search for blocks with data that are not provided in Microsoft Outlook. Such hidden blocks with user data can appear when running Microsoft Outlook when optimizing data storage or after user data.


For example, the user received an unwanted email or the content of the message is confidential and must be removed. In this scenario, the Microsoft Outlook user presses the Delete button, and the email stops in the mail program. When the Delete button is destroyed, Outlook deletes the letter / contact / journal or other objects from the object list. But blocks with deleted message data remain in Microsoft Outlook storage (in PST / OST files). Outlook Forensic Toolbox finds such data blocks, analyzes their content, and, using complex forensic analysis algorithms, recreates the object in whole or in part.
Requirements:
- Windows 98/Me/2000/XP/Vista/7/8/10/11 or Windows Server 2003/2008/2012/2016 and above
Notes:In some cases, it is not possible to completely recreate the object, since all 100% of the blocks with information about the object are not always enough for any reason (overwritten in the file with other data, the link to the nested object is lost, etc.). In case of incomplete recovery of a deleted object, separate files are saved with what was identified and reconstructed.
FAQ-Wiki:
When recovering deleted objects from a PST file using Outlook Forensic Toolbox, some emails end up lacking some of their content. That is, emails have From, To, and Subject fields, but no email body and/or attachments
Answer:
Every object saved by Outlook to a file is stored in several blocks of up to 512 bytes. When a message is deleted, these blocks are not deleted and remain in the file. However, when new emails are sent or received, these blocks may be overwritten. As a result, the deleted email can be recovered only partially, for example:
- if there is a subject, the message body or attachments may be lost;
- if the subject is lost but the body is there, the email will be restored without From and To fields;
- if the message subject and body have been overwritten, the attachment will be saved as a standalone file;
- and so forth.
Outlook Forensic Toolbox does everything possible to recover deleted data. If an object's data blocks are overwritten by Outlook, the object will be recovered only partially.
Screenshots:
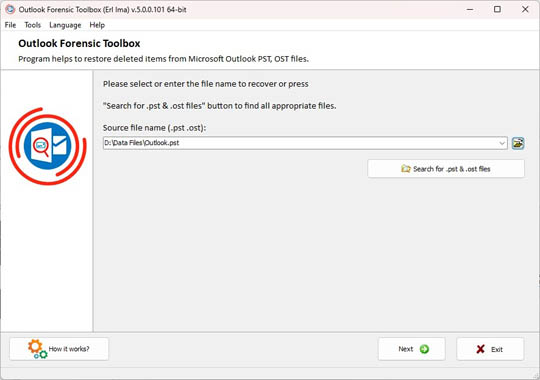
Selecting *.pst file for recovery
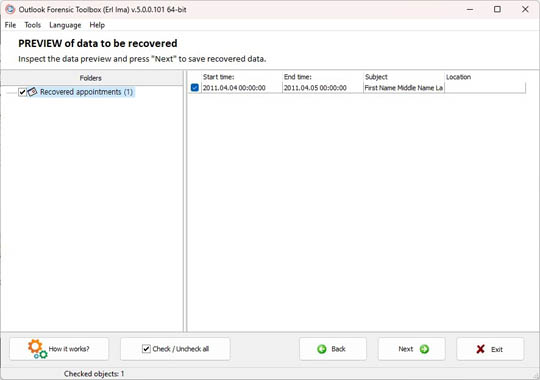
Preview of recovered data
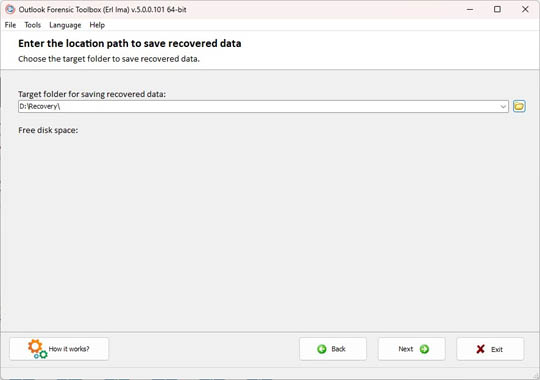
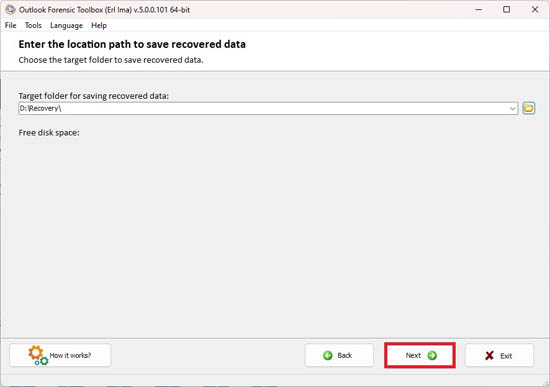
Selecting a path to save the recovered data
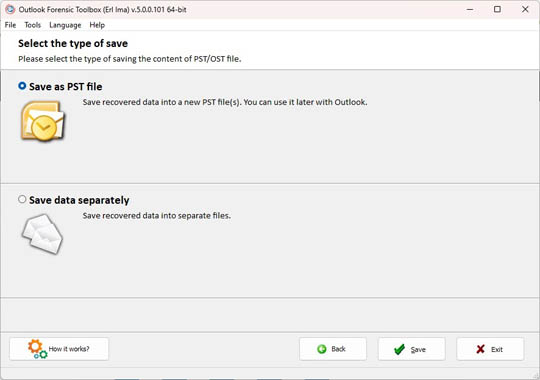
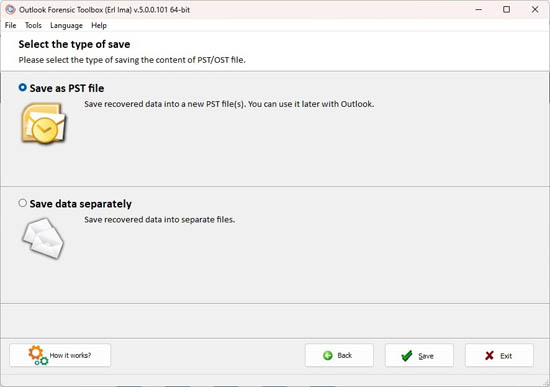
Selecting the type of saving the recovered data
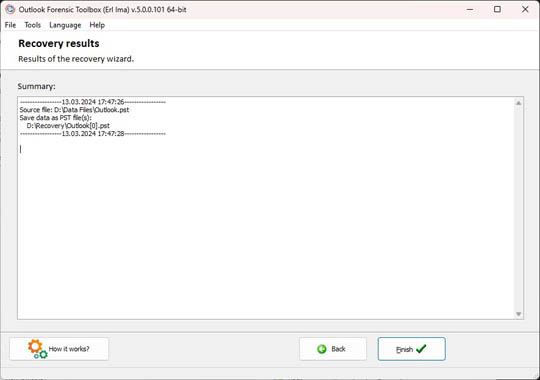
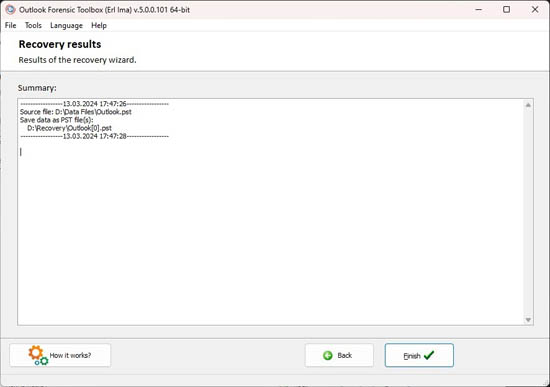
Recovery results
How it Works:
Download software from website. Download
Start Install software:
- Press on downloaded installation file in browser
- Select a downloaded installation file in Windows Explorer and press Enter or double click on it.
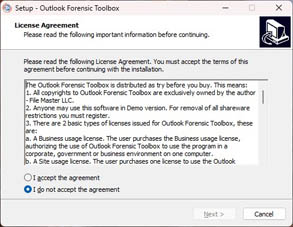
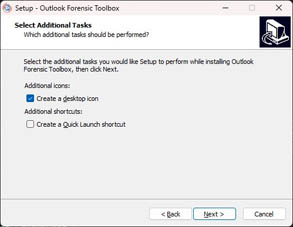
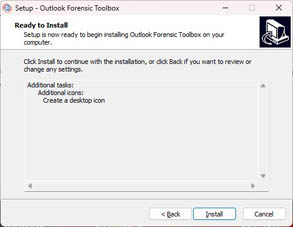
Run installation wizard:
Run program:
- Double click on icon on desktop:
- or
- Select from main menu: Start | Programs | Outlook Forensic Toolbox | Outlook Forensic Toolbox
Select the corrupted *.pst file:
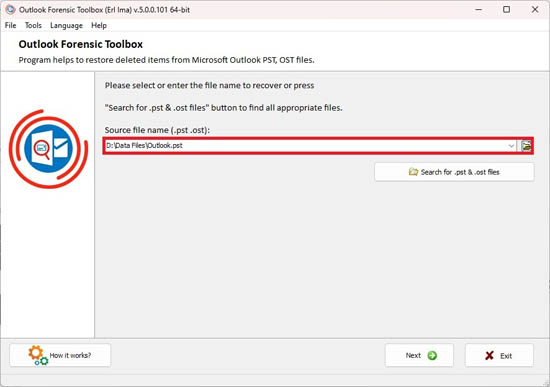
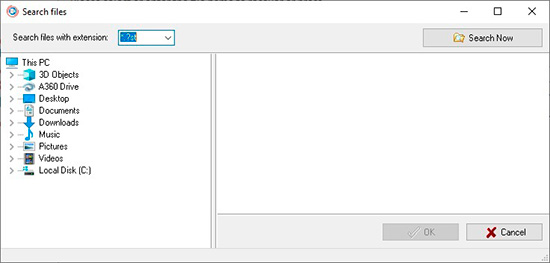
Select the corrupted file from your Microsoft Mail profile or from disk:
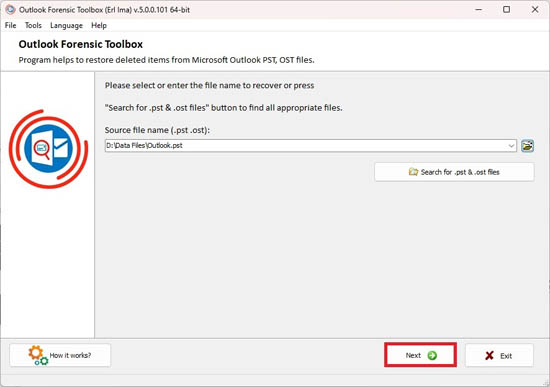
Click Next:
Confirm the start of recovery:
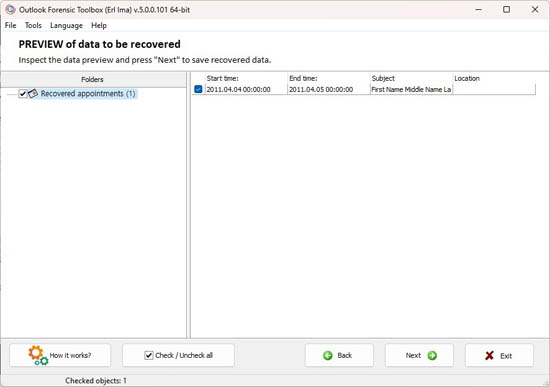
Review and select the recovered objects to save:
Click Next:
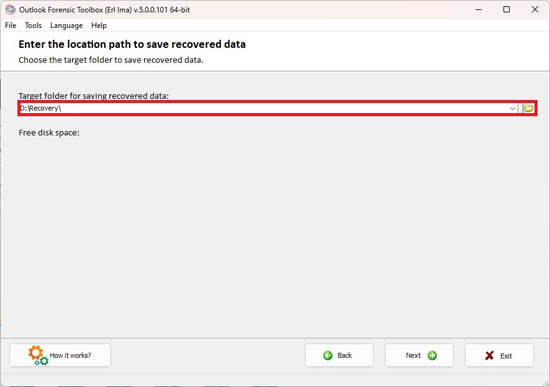
Select a folder for saving:
Click Next:
Select the type of saving:
Recovery results:
Online help:
To identify deleted or hidden data from files with PST or OST extensions, which store Microsoft Outlook data, you need to use the Outlook Forensic Toolbox tool (Download). Outlook Forensic Toolbox is designed as a simple step-by-step guide.
Detailed description of each step:
Step 1. Selecting a source file for forensic analysis
The source file for forensic analysis can be selected in one of 2 ways:
- Press the button
 and select the PST / OST file on disk in Explorer / Windows Explorer. By default, the program offers to analyze the main PST file of the main profile.
and select the PST / OST file on disk in Explorer / Windows Explorer. By default, the program offers to analyze the main PST file of the main profile. - Press the button
 to search for all available data files on the local or network drive.
to search for all available data files on the local or network drive.
Step 2. Forensic analysis of the file
After selecting a file for analysis, you just need to click the Next button and the process of forensic analysis of the file will start automatically. This process can take a long time, depending on the size of the source file and the performance of your computer. Upon completion of the file analysis, all hidden and deleted objects will be displayed on the preview page as a tree of objects and a list of objects from each folder:
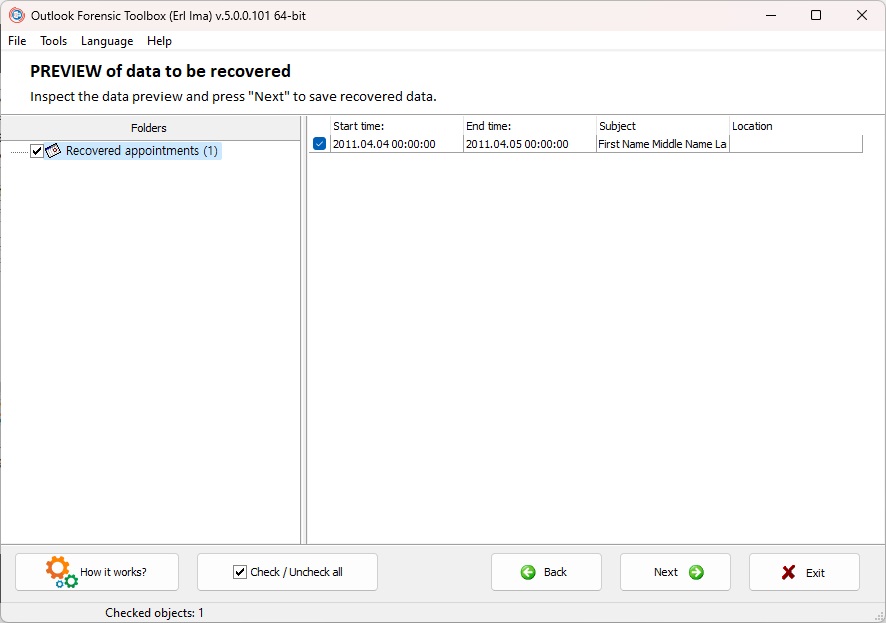
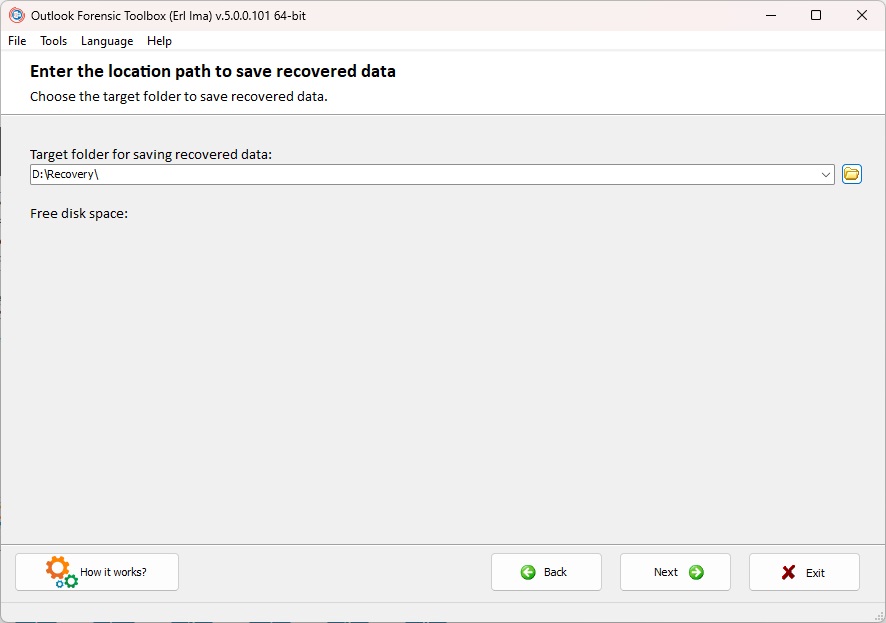
Step 3. Selecting a folder to save data
To save the recovered hidden data, the user needs to choose the folder to save on the local device:
The data will be saved to a PST file so that it will be convenient to open the file in Microsoft Outlook later.
Step 5. Opening the recovered data in Microsoft Outlook
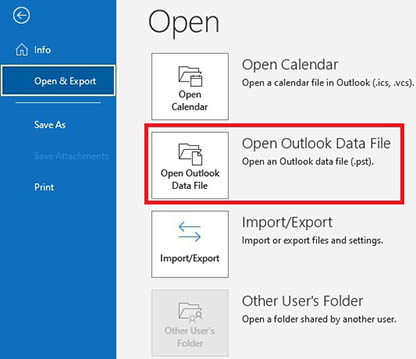
To open a PST file in Microsoft Outlook, you need:
- Select File from the menu
- Select Open and Export
- Select Open Outlook Data File
- In Windows Explorer open the saved .PST file with recovered hidden objects
Buying Outlook Forensic Toolbox:
Business License
for legal use in enterprise, commercial and governmental environments
Site License
for using on several computers of the customer (up to 100 electronic devices) in one building or distributed between several buildings
- An email with a registration code and instructions for activating this code will be sent to the user immediately after the payment confirmation.
- An email with a registration code will be sent from several different mail servers to prevent messages from appearing in SPAM filters. Accordingly, a possible duplication of registration letters received in the user's mailbox.
- To activate the registration code, you need to run the application in Windows under a user with Administrator rights.
- The number of Business or Site licenses activated simultaneously must not exceed the number of purchased licenses.
- We sell software via registration services PayPro Global. That is why not Recovery Toolbox, but the corresponding company will be specified in the payment documents.
The purchased registration key is valid for all 5.x versions of Outlook Forensic Toolbox.
Buying the License Renewal
Business License - 1 Year prolongation
for legal use in enterprise, commercial and governmental environments
Site License - 1 Year prolongation
for using on several computers of the customer (up to 100 electronic devices) in one building or distributed between several buildings
Payment Services:

PayPro Global (PayPro Global, Inc., 250 The East Mall street, Etobicoke, ON Canada, M9B 0A9) is the fastest growing eCommerce company that develops customized solutions to help software producers to easily and effectively sell software online. PayPro Global supports more than one hundred currencies, all major credit cards, and a wide variety of payment options. PayPro Global offers efficient customer support 24/7 and provides personal attention to customers having special requirements.
Customer's reviews and ratings:
good
Best software,useful for all ,sir I am in search of this type of soft - i am using ,so thanks for this one
Great
it's great
excelente aplicativo
good app
good software i like it
Nice neat and Hand recovery tool
It is verry good
Good App
This program found a lot of hidden in PST file. Many pieces of data and requires additional analysis.